Updated features include
Over 140 new SAP specific threat detection cases
Updated noise reduction engine – eliminated over 98.1% of false positives and reduced work
Easier SAP connectivity with QRadar, ArcSight and Splunk
SAP server diskspace optimization with automated SAP security audit log compression & retention
User behavior analytics for SAP – auto detection of suspicious activity
Best practice runbooks for efficient SAP security event classification and tagging
Ready to Run
ETM comes preconfigured with hundreds of SAP specific attack detection rules including those that monitor for unauthorized access to critical data, exploitation of vulnerable SAP functions, malicious usage of debug privileges, and unauthorized creation of users.
Adapts to Your Systems
ETM adapts to users’ SAP usage patterns and business practices. With machine learning, wizards, and automatic suggestions, it guides you through configuring your standard business behavior, eliminating false positives, and providing high quality results.
Regularly Updated
ETM is automatically updated based on ESNC’s continuous research which finds the latest SAP specific threats, latest publications and ESNC’s zero-day SAP attack signatures. ETM customers benefit from always being able to use the latest features and most current SAP threat detection signatures.
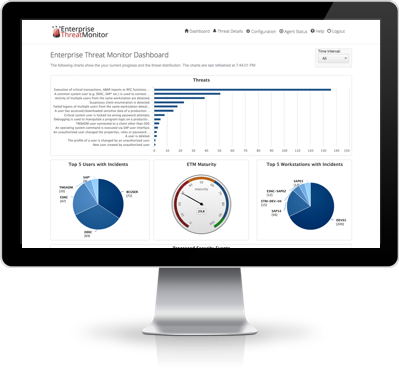
How does Enterprise Threat Monitor work?
The real-time SAP threat detection using ETM works like this:
Events include SAP security logs, system logs, SAP change documents, transport records, user master data changes, SAP security configuration, ESNC’s fraud related analysis results and many others.
The attack correlation engine is developed based on information from ESNC’s research and its collaboration with top clients. It learns and adapts, eliminating the false positives.
The result is high quality, accurate threat assessment.
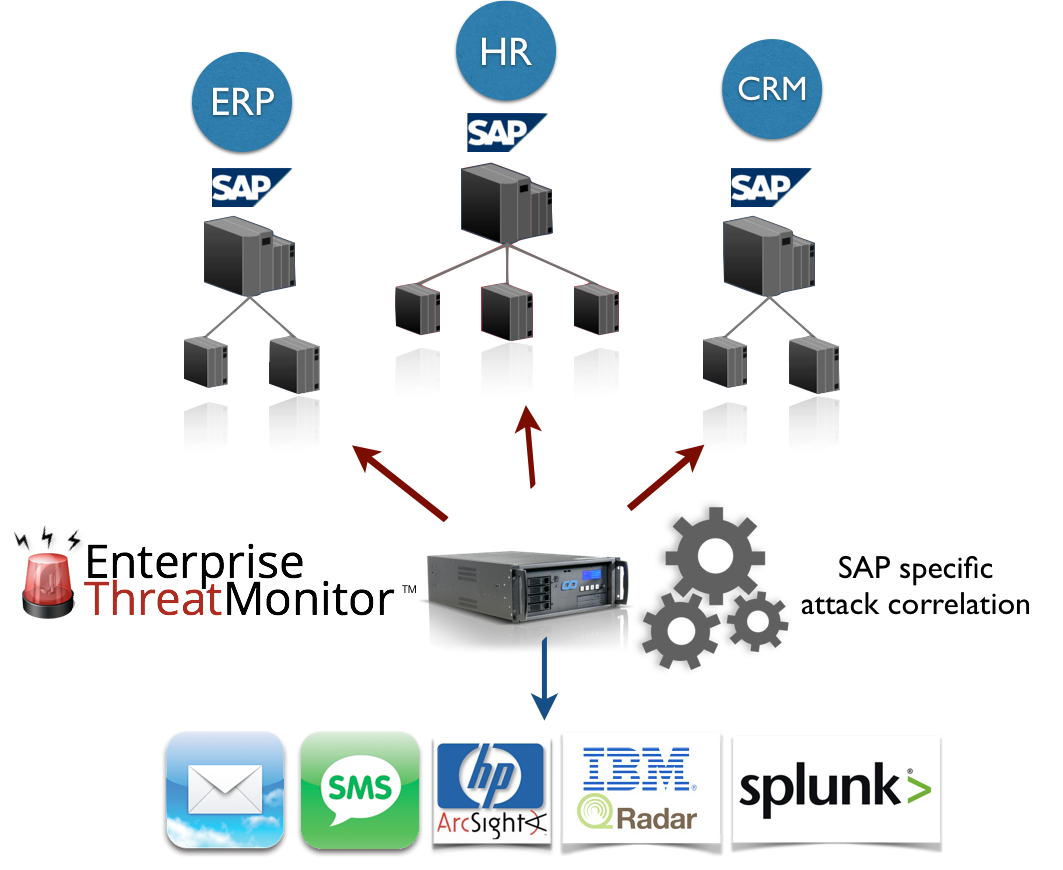
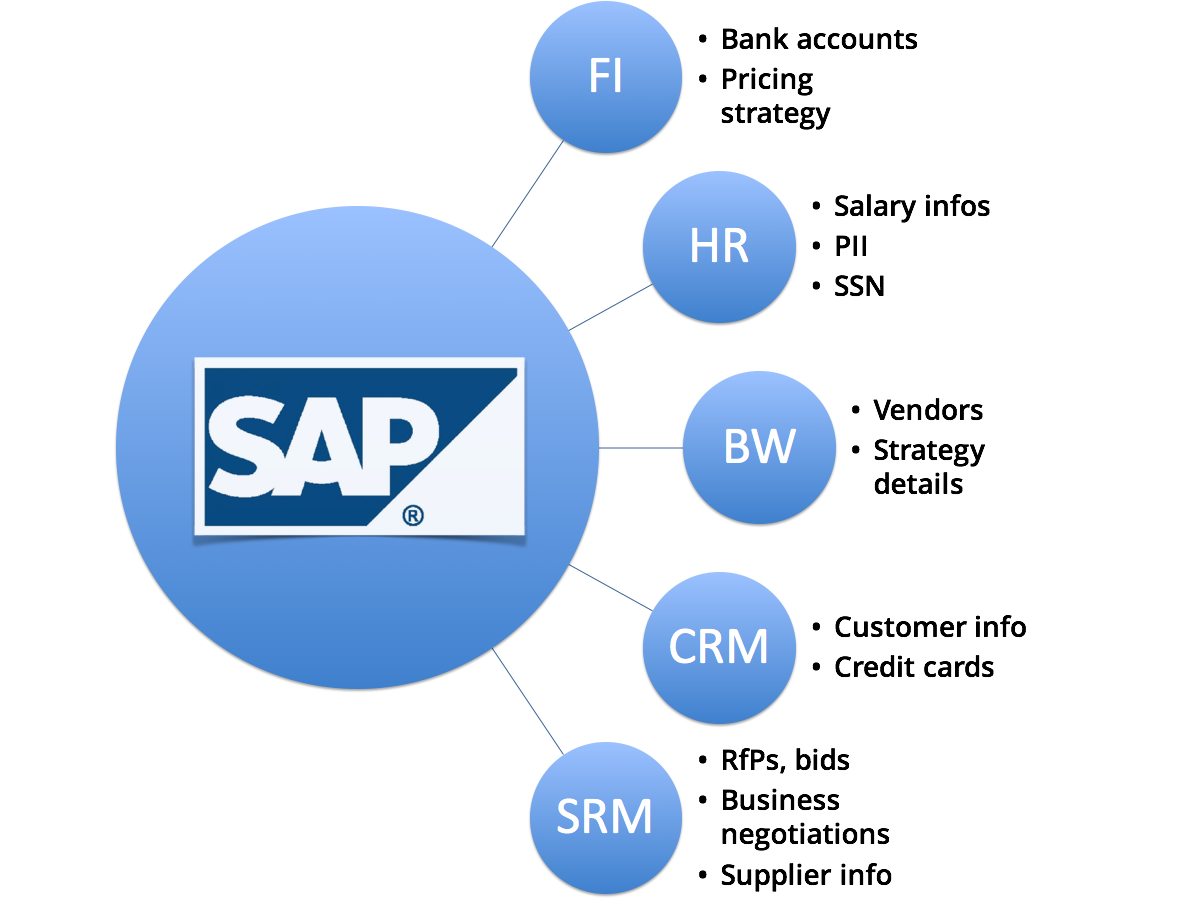
Why do I need real-time SAP security monitoring?
Security breaches are costly. The breach of USIS, the biggest commercial provider of background investigations to the US government, caused company to lose its largest contract and file bankruptcy. The breach of the Target department store chain cost the company over $160 million USD.
SAP applications store and process sensitive business data. Critical business processes including approval processes utilize SAP systems.
Any enterprise with SAP applications will be using it to transact with sensitive data.The prevention efforts (hardening, patching and audits) are not sufficient to protect complex SAP environments. Therefore, most common compliance frameworks mandate security monitoring.
ESNC’s Enterprise Threat Monitor for SAP applications allows companies to react and neutralize incidents before they escalate. This allows building a safety net and satisfying audit requirements related to security monitoring.
Enterprise Threat Monitor Add-ons
SIEM Integration
This add-on allows forwarding correlated ETM events to SIEM solutions such as Splunk, HP ArcSight, or IBM QRadar. It can be purchased additionally, and with this option, you get high quality SAP-specific events directly in your SIEM solution.
“Ask an Expert”
Ideal for SOC teams which lack expert SAP skills, this option allows live communication with SAP security expert for any questions related to ETM or your specific incident with a click of a button through the ETM portal interface.
What is SAP Security Audit Log? How much disk space is required for our system?
Please see the link for detailed information about the SAP security audit log and sizing requirements.
How can I archive the SAP security logs centrally?
Enterprise Threat Monitor supports automated archiving SAP security audit logs and storing them outside SAP, so that you don’t have to keep them on the expensive storage of the SAP system. This allows better protection against attackers who could manipulate logs and reduced costs for data retention. We use a proprietary method for storing the logs locally in a compressed format, which results in over 98% of space savings.
Do I need a SIEM infrastructure for getting real-time SAP security alerts?
No. Enterprise Threat Monitor works alone and it has a very intuitive workflow for SAP security exception management. You don’t need any SIEM (security information and event management) infrastructure. But if you have the infrastructure, processes and people, you can configure ETM to forward real-time SAP security events to it.
Why don’t we just send the raw SAP security logs to SIEM?
For three important reasons:
1- SIEM solutions are not specialized in SAP security events like we are. ETM contains hundreds of threat monitoring cases specific to SAP applications, including zero-day signatures for emerging threats. ETM is regularly updated and allows customizations specific to SAP. Many logs obtained from SAP require further parsing, analysis and correlation before they give out usable information.
2- SAP systems are noisy. ETM solves the noise challenges by leveraging machine learning and adaptive noise reduction. At a recent customer implementation, this resulted in reduction of over 98% of false positives. If you’d like to process raw logs on your own, you should consider these challenges.
3- Sending raw logs may increase your SIEM costs. SIEM solutions typically use EPS (events per second) for pricing calculations. ETM’s pre-correlated, high quality events are significantly low in volume compared to raw logs, e.g. during a recent implementation, ETM forwarded around 3,000 events, after analyzing more than 1,000,000,000 SAP security logs. That’s over 99.999% less events.
Does Enterprise Threat Monitor Support forwarding raw security event logs?
Yes, ETM supports raw SAP security audit log event forwarding.
Can’t we write our own rules in our SIEM system for analyzing SAP logs?
Yes, you can write some rules. However, this can result in less quality and higher costs because of the following reasons:
1 – Maintaining & updating enterprise threat detection cases specific to SAP is costly
ETM includes hundreds of rules built-in. These rules are professionally maintained and updated based on the changing threat landscape. It took us more than 6 years and multiple large scale customer implementations to build this knowledge.
Typical enterprises do not have the skilled people required for this specialized type of upkeep. And if they do, these people are very difficult to replace when they leave the company.
2 – Eliminating false positives and noise is a big challenge
One of the biggest challenges of threat monitoring is eliminating false positives and reducing noise. Enterprise Threat Monitor uses propriety techniques, including machine learning for learning from organizational patterns and eliminating noise.
At a recent customer implementation, Enterprise Threat Monitor saved over 130 man days of work using its adaptive learning capabilities. You can find more information about this by requesting our customer success stories.
What is SAP SIEM?
SAP SIEM is efficient review and management of SAP specific security events. Typical SIEM solutions focus on OS and network logs and therefore they do not have in-depth understanding of SAP internals and processes.
Which SIEM solutions does ETM support?
ETM builds the gap between SAP and traditional SIEM. It supports all popular SIEM solutions available in the market. It is most commonly used with HP ArcSight, IBM QRadar and Splunk. You can find more information for SAP SIEM connectivity here.
Does ETM support native interfaces and formats for SIEM integration?
Yes, ETM uses Splunk’s native HTTPs event collector for sending SIEM events to Splunk Enterprise and HP ArcSight’s CEF format to communicate with ArcSight SIEM systems. For IBM QRadar, ETM uses QRadar’s Leef format for sending real-time SAP security events. For McAfee SIEM SAP connectivity and other SIEM solutions, it uses CEF, LEEF, and syslog format.
How does SAP QRadar, Splunk or ArcSight integration work?
SAP Splunk integration is as simple as configuring a few steps for sending the pre-correlated events. SAP QRadar integration may require some effort importing LEEF format events and mapping event properties and QRadar QIDs. SAP ArcSight integration may also require basic configuration.
Should I be sending raw SAP events to SIEM?
This may increase your SIEM EPS (events per second) costs unnecessarily. Enterprise Threat Monitor sends precorrelated information to SIEM solutions and compresses/archives SAP logs automated for quality, cost efficiency, and optimized resource usage.
What is EU General Data Protection Regulation (GDPR) and SAP? What are the first things to do for GDPR?
The following recommendations list the top 3 things to do for SAP and GDPR. SAP systems require certain processes to be introduced for compliance with EU GDPR and this includes critical topics such as protecting SAP systems, SAP data retention, SAP SIEM integration, and notification of the SAP breaches within 72 hours. Please contact us regarding our GDPR readiness assessment tool which allows preparing your SAP systems and ABAP code for GDPR using an efficient methodology.
What is 23 NYCRR 500 and SAP? How to Address New York State Proposed Cybersecurity Requirements For Financial Services Companies Related to SAP Applications?
NYCRR 500 requires financial services companies to introduce an SAP cybersecurity program which includes execution of periodic SAP security assessments, detection of enterprise threats in SAP applications, responding to detected threats, and fulfill reporting obligations. Companies which use ESNC services and Enterprise Threat Monitor can achieve compliance of these requirements.