Efficient Security Response Methodology for Integrating SAP Security Events into SIEM
This methodology is developed by ESNC to address shortcomings of the incident response and security exception management processes while implementing SIEM solutions which focus on application security events.
The objective of this methodology is to minimize the number of specific security exceptions and maximize the number of generic security exceptions so that the false positives of the underlying security event management system can be reduced.
This methodology recommends classifying security events based on three categories during a review session:
Three Categories
A- Business process deficiency
In a security event management system, there may be many events similar in nature, which cannot be tied to a specific person.
When you see many events such as different users, downloading SAP customer master data to their desktops for using local tools such as Excel to analyze them, then the root cause must be addressed.
This type of events must be categorized as business process deficiency and the managers responsible for these users must be contacted to understand the process better. If this shows a business process issue e.g. the users have to do it because this is how they generate CRM reports, then mitigating controls must be in place to address this issue and process engineers or process owners must be contacted to improve the security of this process.
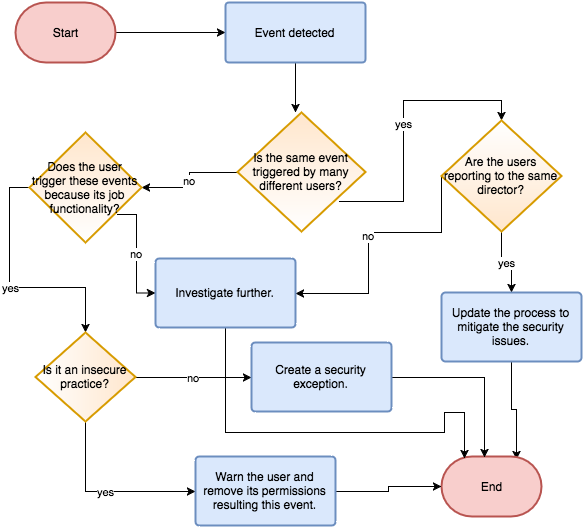
B- User working in non-secure/non-compliant way
There may be certain SAP power-users which may be using system functionality or certain service accounts, instead of their own users during their regular business day. When these incidents are discovered, user must be warned and the authorizations of the user must be readjusted accordingly. If it becomes apparent that the user possesses the credentials of a system user, the password of this user must be also updated.
C- Potential “real” incident: Suspicious activity by user
When it is apparent that the event results from suspicious activity, the regular incident response process must be triggered for further analysis.
Which type of the above categories create the most noise?
Process deficiencies and users working in non-secure way are the most common reason of many security related events in the SIEM system. Resolving them will result in significant reduction in noise.
Potential real incidents require the most amount of time for analyzing the incident and doing forensics. However the amount of events will be much less compared to the above two.
How does Enterprise Threat Monitor support the ESR methodology?
Enterprise Threat Monitor is built with ESR methodology in mind and ETM’s security exception workflow and threat labelling features allow effortless implementation of the ESR methodology.
